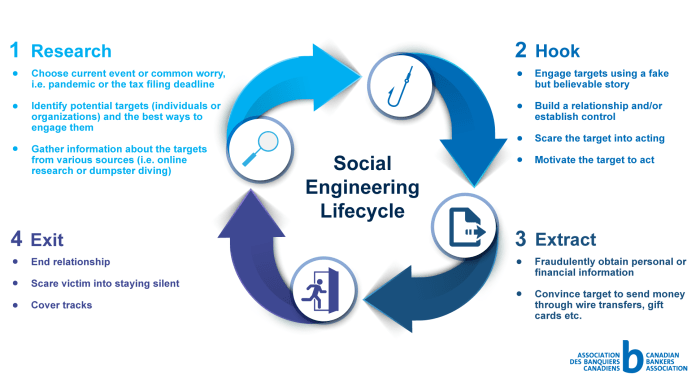
Social engineering attacks prey on human vulnerabilities, exploiting inherent weaknesses in our psychology and behavior to manipulate us into divulging sensitive information or taking actions that compromise our security. These attacks are meticulously crafted to bypass technical safeguards and target the human element, making them a formidable threat to individuals and organizations alike.
In this comprehensive guide, we will delve into the intricate world of social engineering, exploring the methods employed by attackers, the vulnerabilities they exploit, and the devastating consequences they can inflict. We will also provide practical mitigation strategies and case studies to empower readers with the knowledge and tools necessary to safeguard themselves and their organizations from these insidious attacks.
Defining Social Engineering Attacks: Social Engineering Attacks Prey On Human Vulnerabilities
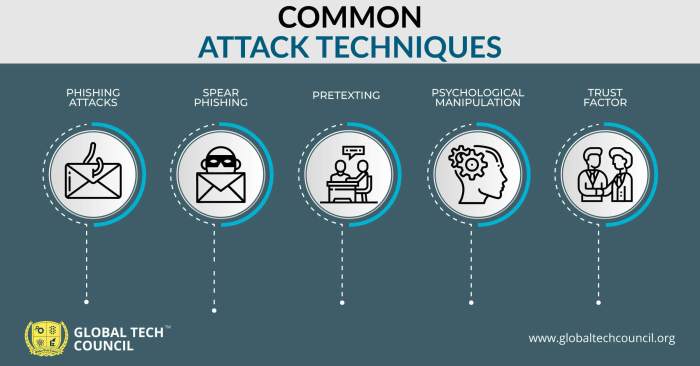
Social engineering attacks are a form of cybercrime that relies on human interaction to exploit vulnerabilities in security systems. Attackers manipulate individuals into divulging sensitive information or performing actions that compromise the security of their systems or organizations.
Common social engineering techniques include:
- Phishing: Sending emails or text messages that appear to be from legitimate sources, tricking recipients into clicking on malicious links or providing personal information.
- Vishing: Making phone calls that mimic legitimate businesses or organizations, attempting to obtain sensitive information over the phone.
- Baiting: Leaving physical devices or USB drives in public places, enticing individuals to connect them to their computers and infect them with malware.
Human vulnerabilities play a significant role in the success of social engineering attacks. Individuals are often susceptible to manipulation due to cognitive biases, such as:
- Trust: People tend to trust others and may be more likely to comply with requests or provide information if they believe the requester is legitimate.
- Authority: Individuals may be more likely to follow instructions from someone they perceive as an authority figure, such as a CEO or a government official.
- Urgency: Attackers often create a sense of urgency to pressure individuals into making quick decisions without fully considering the consequences.
Identifying Human Vulnerabilities
Common human vulnerabilities exploited by social engineering attacks include:
- Trust: People tend to trust others and may be more likely to comply with requests or provide information if they believe the requester is legitimate.
- Authority: Individuals may be more likely to follow instructions from someone they perceive as an authority figure, such as a CEO or a government official.
- Urgency: Attackers often create a sense of urgency to pressure individuals into making quick decisions without fully considering the consequences.
- Curiosity: Individuals may be tempted to click on links or open attachments out of curiosity, even if they are suspicious.
- Fear: Attackers may use fear to manipulate individuals into taking actions they would not normally consider, such as providing their passwords or financial information.
These vulnerabilities make individuals susceptible to attacks because they can cloud judgment and lead to impulsive or irrational decisions.
Methods of Exploitation, Social engineering attacks prey on human vulnerabilities
Attackers use various methods to exploit human vulnerabilities in social engineering attacks. Some common methods include:
- Phishing emails: Attackers send emails that appear to be from legitimate sources, such as banks or online retailers. These emails often contain links to malicious websites or attachments that can infect computers with malware.
- Vishing calls: Attackers make phone calls that mimic legitimate businesses or organizations. They may attempt to obtain sensitive information over the phone, such as passwords or credit card numbers.
- Baiting: Attackers leave physical devices or USB drives in public places, enticing individuals to connect them to their computers. These devices can be infected with malware that can spread to the individual’s computer.
- Social media attacks: Attackers use social media platforms to target victims. They may create fake profiles or send messages that appear to be from friends or family members. These messages may contain links to malicious websites or requests for personal information.
Attackers often use a combination of these methods to increase their chances of success.
Consequences of Social Engineering Attacks
Successful social engineering attacks can have significant consequences for individuals and organizations. These consequences include:
- Data breaches: Social engineering attacks can lead to data breaches, exposing sensitive information such as customer records, financial data, or trade secrets.
- Financial losses: Attackers can use social engineering techniques to steal money from individuals or organizations. They may trick victims into providing their bank account information or credit card numbers.
- Reputational damage: Social engineering attacks can damage an organization’s reputation. If customers or partners lose trust in an organization’s ability to protect their data, they may be less likely to do business with them.
In addition to these consequences, social engineering attacks can also lead to psychological distress for victims. They may feel embarrassed or ashamed if they have been tricked into providing sensitive information. They may also worry about the potential consequences of the attack, such as identity theft or financial loss.
Mitigation Strategies
There are a number of steps that individuals and organizations can take to mitigate the risk of social engineering attacks. These steps include:
- Security awareness training: Educate employees about social engineering attacks and how to recognize them. This training should include information on common social engineering techniques, such as phishing emails and vishing calls.
- Multi-factor authentication: Implement multi-factor authentication for all sensitive accounts. This requires users to provide two or more forms of identification when logging in, making it more difficult for attackers to gain access to accounts.
- Technical controls: Implement technical controls to block phishing emails and vishing calls. These controls can include email filters and call screening software.
- User education: Educate users about the importance of protecting their personal information. This includes teaching them how to recognize phishing emails and vishing calls, and how to protect their passwords and other sensitive information.
By following these steps, individuals and organizations can reduce the risk of social engineering attacks and protect their sensitive information.
Clarifying Questions
What are the most common social engineering techniques?
Phishing emails, vishing calls, spear phishing, pretexting, baiting, and scareware are among the most prevalent social engineering techniques.
How can I protect myself from social engineering attacks?
Be cautious of unsolicited emails and phone calls, never click on suspicious links or open attachments, use strong passwords and enable two-factor authentication, and report any suspicious activity to the appropriate authorities.
What are the potential consequences of a successful social engineering attack?
Social engineering attacks can lead to data breaches, financial losses, reputational damage, identity theft, and other severe consequences.